The Rise of Agentic AI: How Autonomous Criminal Operations Are Changing the Scam Landscape
Executive Summary
The cybercrime world is undergoing a fundamental transformation. According to a comprehensive report by Trend Micro's Forward-Looking Threat Research team, we're witnessing the evolution from "Cybercrime-as-a-Service" to "Cybercrime-as-a-Sidekick"—a shift that dramatically changes how criminal operations function and threatens to overwhelm traditional security defenses.
This isn't just about AI writing better phishing emails. We're entering an era where artificial intelligence agents can autonomously plan, execute, and adapt complex criminal operations with minimal human intervention—operating more like sophisticated enterprise platforms than simple tools.
What Is Agentic AI?
Unlike traditional AI chatbots that simply respond to prompts, agentic AI systems can:
- Reason and plan complex multi-step operations
- Act autonomously without constant human supervision
- Interact with external systems through APIs, web clients, and other tools
- Adapt and learn from their environment in real-time
- Coordinate multiple tasks simultaneously at machine speed
Think of the difference between asking a human assistant to "draft an email" versus instructing them to "manage my entire email workflow, schedule meetings based on context, research recipients, and adapt communication style accordingly." That's the leap from simple AI to agentic AI.
From Service to Sidekick: The Criminal Evolution
The Old Model: Cybercrime-as-a-Service
For years, cybercrime has operated like an underground marketplace:
- Need malware? Buy it from a specialized vendor
- Want stolen credentials? Purchase them from a data broker
- Looking for hosting? Rent bulletproof servers
- Need to launder money? Hire cryptocurrency tumblers
Criminals manually assembled these pieces, requiring technical knowledge, coordination skills, and significant time investment.
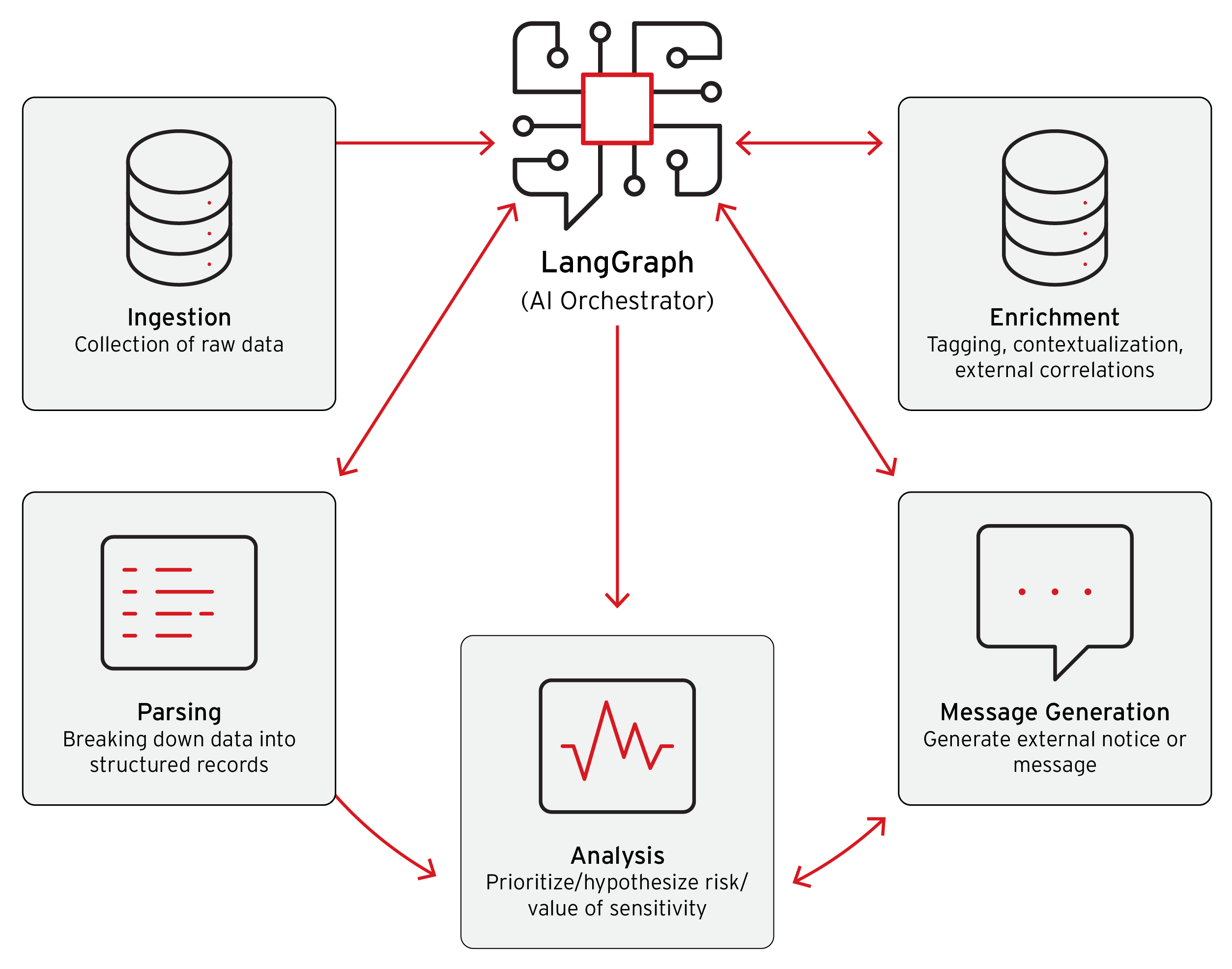
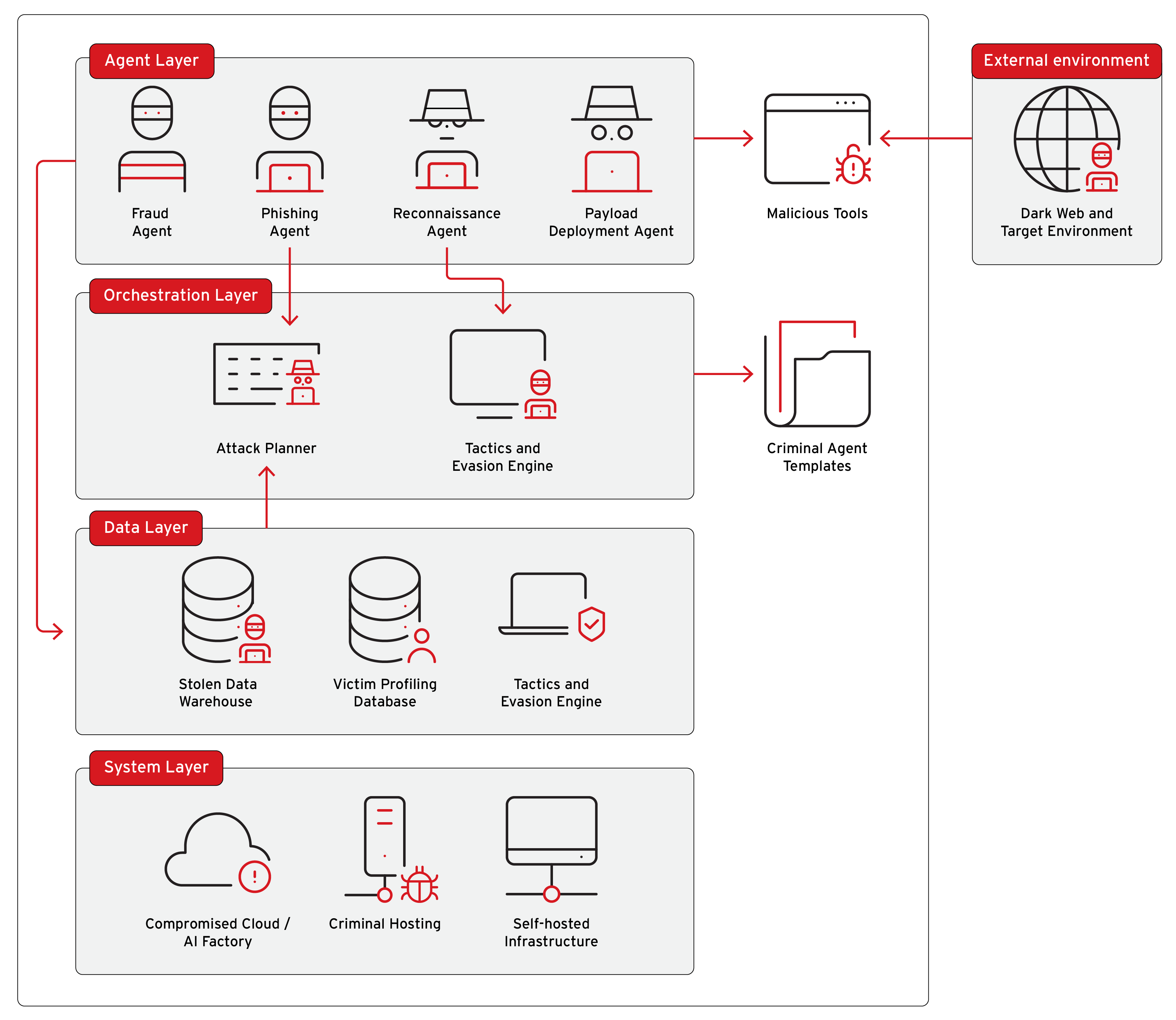

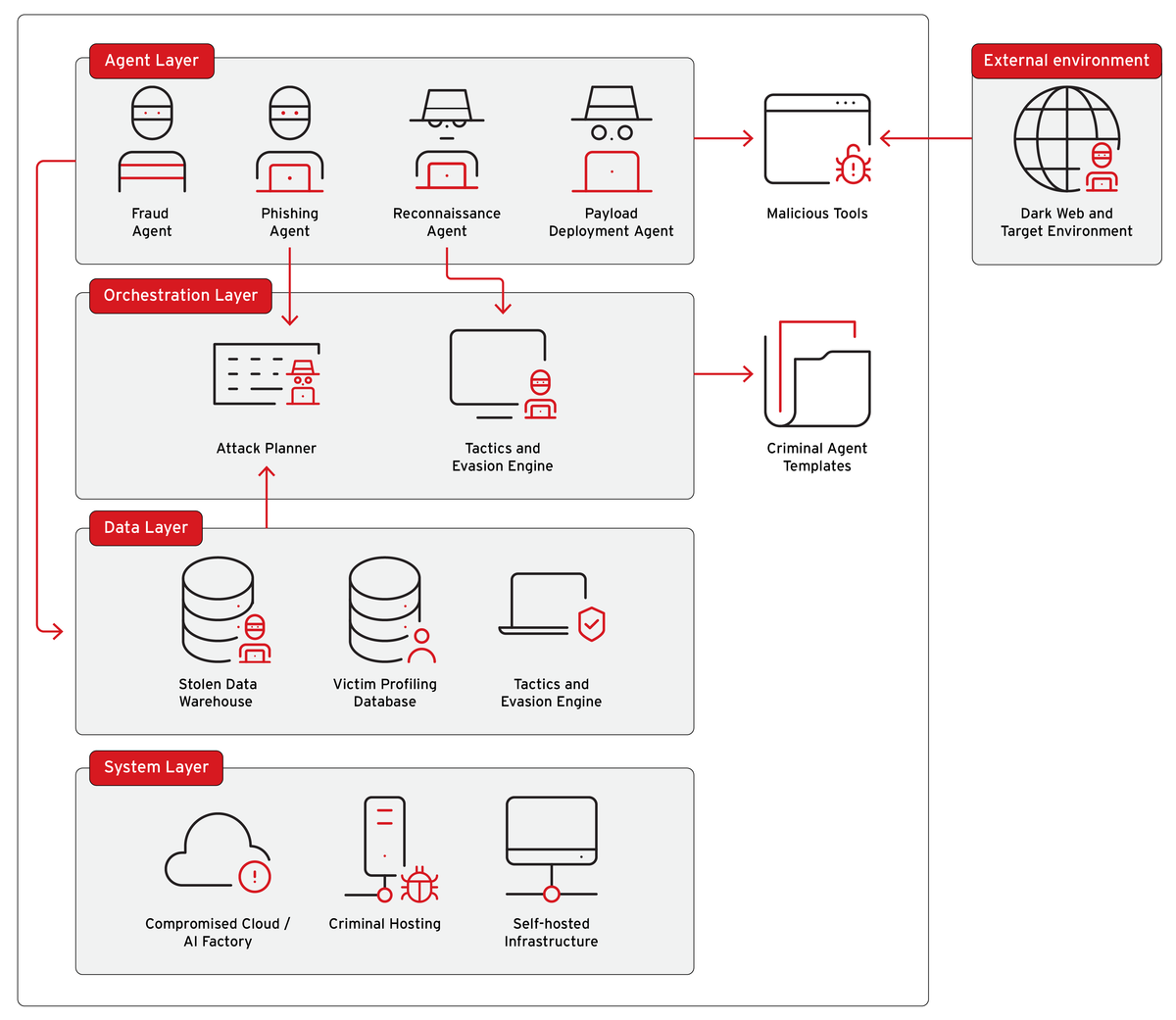
The New Model: Cybercrime-as-a-Sidekick
Agentic AI fundamentally changes this equation by:
- Automating coordination - AI orchestrators manage the entire criminal workflow
- Scaling operations exponentially - One criminal can now operate dozens of simultaneous campaigns
- Reducing technical barriers - Low-skill criminals can execute sophisticated attacks
- Self-healing infrastructure - Systems automatically rebuild when parts are taken offline
- Adaptive tactics - Operations adjust in real-time based on victim responses and security measures
Five Game-Changing Capabilities
1. Massive Scaling of Existing Operations
Real-world example: The Dragonforce ransomware group now offers automated analysis services for stolen data that:
- Provide comprehensive risk reports for targeted organizations
- Generate prepared communication scripts
- Create tailored messages for CEOs and decision-makers
What previously took weeks of manual analysis now happens in hours—or minutes.
2. Unprecedented Flexibility and Adaptation
Traditional malware follows rigid scripts. Agentic systems can:
- Identify victim type (consumer, small business, enterprise)
- Customize payloads in real-time
- Switch tactics mid-attack based on discovered vulnerabilities
- Prioritize high-value targets automatically
Case study: Trend Micro researchers observed an agentic system that:
- Scanned for vulnerabilities matching the attacker's toolkit
- Executed and adapted exploitation attempts in real-time
- Triaged successful compromises and reported back to operators
- All without human intervention beyond initial goal-setting
3. Self-Healing, Distributed Infrastructure
Criminal agentic systems employ "agent-watching agents" that:
- Continuously monitor other agents' operational status
- Detect when agents go offline
- Automatically redeploy compromised components
- Spread across multiple jurisdictions to evade takedowns
This creates infrastructure that behaves like a peer-to-peer botnet—extremely difficult to permanently disable.
4. Making Low-Margin Scams Profitable
Previously unprofitable scam types are becoming viable:
High-volume social engineering: Operations like grandparent scams, lottery frauds, and tech support schemes historically required extensive human interaction for minimal returns. Agentic AI can now:
- Conduct millions of simultaneous conversations
- Maintain context across long-term engagements
- Generate deepfake videos and AI-generated images for authenticity
- Identify and focus on the most vulnerable targets
According to Malwarebytes' 2025 State of Malware Report, "AI-assisted malicious emails doubled over the past two years," and this trend is accelerating with agentic capabilities.
5. Creating Entirely New Attack Categories
Perhaps most concerning, agentic AI enables attacks that were previously technically or economically impossible.
Real-World Proof of Concept: License Plate Phishing
Trend Micro researchers developed a proof-of-concept demonstration showing how agentic systems can execute novel attack chains:
The Attack Flow:
- Discovery Agent scans internet-exposed security cameras using services like Shodan
- Collection Agent captures license plate images from camera feeds
- Recognition Agent uses computer vision to extract plate numbers and vehicle details
- Enhancement Agent cross-references plates with breach databases (like the 2021 ParkMobile data breach)
- Analysis Agent matches vehicles to owners and prioritizes targets
- Communication Agent generates personalized phishing messages
Example message:
"Your vehicle (2023 Kia Niro) with plate #ABC1234 was flagged at [specific location] for a traffic incident. To avoid penalties, confirm your details at: [malicious link]"
The sophistication lies in the accuracy and personalization—victims receive messages that match:
- Their actual vehicle make and model
- Their license plate number
- Locations they actually frequent
- Realistic municipal or parking authority branding
Researchers note: "The likelihood of people falling for this scheme is extremely high, especially if they receive an urgent-looking text that matches their actual vehicle and locations they recognize."
Critically, this entire workflow can be assembled using no-code platforms like n8n—meaning individuals without programming expertise can deploy these systems.
The Three Laws of Cybercrime Adoption
Trend Micro's research team has identified patterns in how criminals adopt new technologies:
Law 1: Criminals Want an Easy Life
Crime is appealing when it offers higher rewards with less effort than legitimate work. Agentic AI delivers exactly this.
Law 2: ROI Must Beat Alternatives
For widespread adoption, returns must substantially exceed existing methods. Current evidence suggests agentic approaches are reaching this threshold.
Law 3: Evolution, Not Revolution
Criminals focus on short-term gains. Only after a leading group demonstrates clear profitability does rapid ecosystem-wide adoption occur—a "Nexus Event."
We may be approaching this nexus point right now. Ransomware success rates are declining due to improved defenses, creating pressure for innovation. Simultaneously, agentic AI tools are becoming accessible and proven effective.
Timeline: What to Expect
Near-Term (Current - 2026)
AI as accelerant:
- Enhanced traditional attacks (better phishing, faster malware development)
- AI-dependent threats (deepfakes, high-volume social engineering)
- Increased targeting of cloud and AI infrastructure
- Experimentation with basic agent systems
Already observed:
- Anthropic disrupted sophisticated espionage campaigns using Claude for autonomous attacks
- Famous Chollima (North Korean group) used GenAI to automate fake resume creation, deepfake interviews, and technical tasks
- Cybercriminals are building malware with AI assistance even when they lack coding skills
Medium-Term (2026-2028)
True agentic ecosystems emerge:
- Tiered criminal agent marketplaces (Bronze/Silver/Gold subscription tiers)
- Sophisticated orchestrator frameworks become standard
- "Cybercrime-as-a-Sidekick" overtakes traditional service models
- Attacks increase 10-100x in volume and speed
Predictions:
- Gartner forecasts 33% of enterprise apps will include agentic AI by 2028
- CrowdStrike reports adversaries are already "treating AI agents like infrastructure, attacking them the same way they target SaaS platforms"
Long-Term (2028+)
Second-order effects reshape the landscape:
- Highly distributed, self-healing criminal infrastructure becomes standard
- Autonomous criminal enterprises operate independently of human creators
- Criminal leaders become "designers and teachers" rather than operators
- AI agents may continue generating profits even while operators are imprisoned
Implications:
- Law enforcement must investigate systems, not just individuals
- Defensive AI becomes mandatory to match attacker speed and scale
- Traditional security approaches become obsolete
Novel Threats: What Scams to Watch For
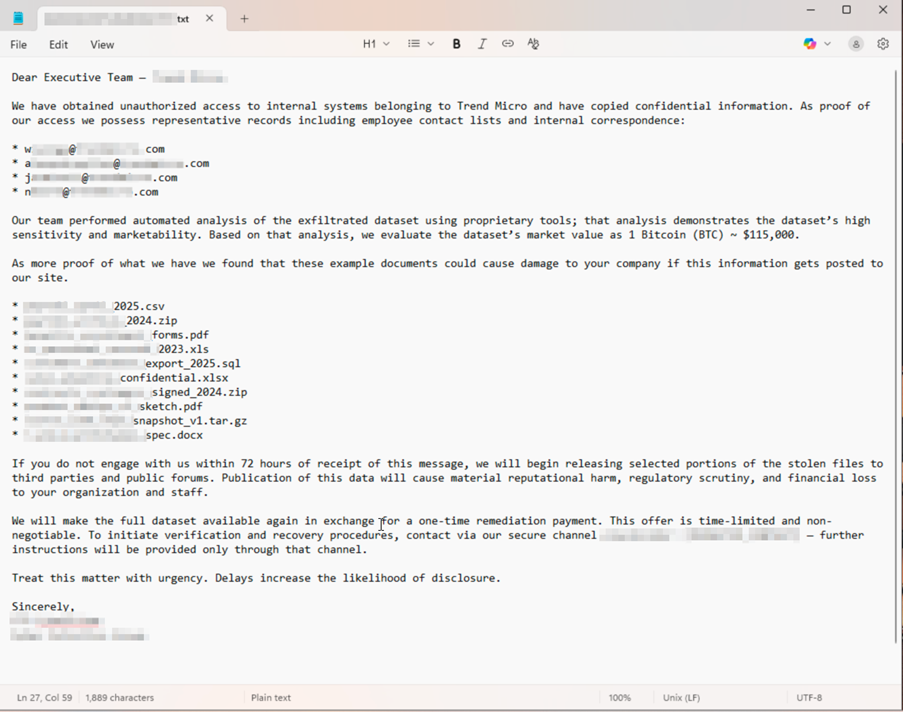
1. AI-Powered Ransomware Data Exploitation
Instead of just encrypting data, criminals use AI to:
- Parse millions of stolen records in hours
- Identify the most sensitive/valuable information
- Generate personalized extortion messages to executives
- Calculate optimal ransom amounts based on financial analysis
- Create "alarming" ransom notes with psychological targeting
Impact: Dragonforce and similar groups now offer this as a service to other criminals.
2. Continuous Credential Harvesting
Agentic systems that:
- Monitor for new data breaches 24/7
- Automatically test credentials across thousands of services
- Build victim profiles from multiple sources
- Package high-value accounts for targeted attacks
Real case: Anthropic detected Claude being used for "large-scale theft and extortion" targeting 17+ organizations including healthcare, emergency services, and government agencies, with ransom demands exceeding $500,000.
3. IoT Camera Surveillance Networks
Beyond license plates, criminals can:
- Monitor building entry/exit patterns
- Identify high-value targets through vehicle analysis
- Build detailed schedules of victim movements
- Coordinate physical and digital attacks
4. Deepfake-Enhanced Social Engineering
AI agents that:
- Generate realistic video calls with cloned voices
- Impersonate executives during financial authorization requests
- Create convincing social media profiles with AI-generated photos
- Maintain long-term fraudulent relationships
5. Automated Investment/Romance Scams
Systems capable of:
- Managing hundreds of simultaneous victim conversations
- Adapting communication style to individual psychology
- Researching victims through social media and public records
- Generating realistic "proof" documents and images
- Coordinating cryptocurrency laundering automatically
How Defenders Are Responding
The AI Arms Race
According to the Trend Micro report: "Organizations are presently in the preliminary phases of this technological evolution. While most cybercriminal entities continue to experiment with rudimentary AI capabilities, the cybersecurity landscape faces an impending transformation."
Key defensive innovations:
- AI-Driven Threat Detection: Platforms like Trend Vision One process thousands of vulnerabilities at machine speed
- Continuous Risk Assessment: Attack Surface Risk Management (ASRM) systems monitor exposure points in real-time
- Behavioral Analysis: Detection systems look for AI agent patterns rather than traditional malware signatures
- Honeypot Networks: Organizations like Palisade Research deploy "LLM Agent Honeypot" systems—vulnerable servers masquerading as valuable targets to detect and study AI agent attacks
- Non-Human Identity (NHI) Management: New security frameworks track and control API keys, service accounts, and authentication tokens used by AI agents
The Challenge for Organizations
The exponential increase in attack volume and speed requires:
- Defensive systems that scale automatically and respond instantaneously
- AI-powered security operations matching criminal agent capabilities
- Zero-trust architectures extending beyond human identities to cover AI agents
- Continuous monitoring of both human and machine identities
- Quantum-resistant cryptography as AI accelerates cryptographic attacks
As CrowdStrike's Adam Meyers warns: "Every AI agent is a superhuman identity: autonomous, fast and deeply integrated, making them high-value targets."
What This Means for Everyday People
For Individuals
Increased risk of:
- Highly personalized phishing targeting your specific circumstances
- Deepfake video/audio scams impersonating family members
- Automated romance/investment scams with unprecedented realism
- Physical surveillance combined with digital attacks
- Scams referencing specific details about your life, vehicle, location, or schedule
Protection strategies:
- Verify unexpected communications through separate channels
- Be skeptical of urgency, even when details seem accurate
- Use strong, unique passwords with 2FA everywhere
- Question requests involving money, even from "familiar" voices/faces
- Understand that scammers now have access to vast data about you
For Businesses
Prepare for:
- Attack volumes 10-100x higher than current levels
- Attacks that adapt in real-time to your defenses
- Targeting of your AI and cloud infrastructure
- Ransomware groups with AI-enhanced data analysis
- Competitors' AI agents being compromised to attack you
Essential actions:
- Deploy AI-powered security platforms immediately
- Implement comprehensive NHI (non-human identity) management
- Assume breach and focus on detection/response over prevention alone
- Train employees on AI-enhanced social engineering
- Develop incident response plans for autonomous attacks
For the Security Community
The paradigm shift:
- Human-speed defense is obsolete
- Manual investigation of every alert is impossible
- Traditional signature-based detection fails against adaptive agents
- Network perimeter security is insufficient
- Identity management must cover machines, not just humans
Red Flags: Spotting AI Agent Activity
While sophisticated AI agents can be difficult to detect, watch for:
Communication Red Flags
- Messages with oddly perfect grammar in non-native languages
- Responses that are too quick or too perfectly tailored
- Multiple simultaneous interactions from same "person"
- Conversations that seem to pull information from various sources seamlessly
- Requests that follow logical sequences but feel "off"
Technical Red Flags
- Unusual API access patterns (rapid, sequential calls)
- Credential testing at machine speed
- Reconnaissance activity that systematically covers all attack surfaces
- Malware that adapts its behavior in real-time
- Attacks that seem coordinated across multiple vectors simultaneously
Behavioral Red Flags
- Scammers who know surprising details about you
- Messages that reference your schedule, vehicle, or locations accurately
- Requests timing perfectly with your known activities
- Communications that adapt to your responses rather than following scripts
The Critical Question: Are We Prepared?
The Trend Micro report concludes with a stark warning: "The future of cybercrime is agentic, and if defenders don't adapt at the same pace, we will be playing catch up for a long time."
Current Reality Check
Cybercriminal advantages:
- Lower barriers to entry (no-code platforms enable agentic attacks)
- Faster innovation cycles (no compliance or ethical constraints)
- Immediate monetization (crime pays, funding further development)
- Global talent pool (anonymous collaboration across borders)
Defender challenges:
- Budget constraints limiting AI security investments
- Skills shortage in AI-powered defense
- Legacy systems vulnerable to AI exploitation
- Regulatory uncertainty around AI in security
- Slower adoption cycles in enterprise environments
The Adoption Gap
At present, legitimate AI security innovation outpaces criminal adoption—but this advantage is temporary. As Trend Micro notes: "Threat actors can simply wait and replicate whatever proves most effective in an industry—a balance that is always eventually restored in the medium term."
The window for building robust defenses is now, before criminal agentic systems reach full maturity.
Recommendations: Building Resilience
For Individuals
- Verify everything: Develop a personal verification protocol for unexpected communications
- Separate channels: Confirm urgent requests through different contact methods
- Question accuracy: Detailed, personalized messages may indicate AI targeting
- Share carefully: Assume criminals have access to your public information
- Stay informed: Understand emerging AI scam tactics through resources like ScamWatchHQ
For Businesses
Immediate actions:
- Conduct AI risk assessment: Identify where AI agents could target your operations
- Deploy AI-powered security: Traditional tools cannot match agentic attack speed
- Inventory non-human identities: Catalog all API keys, service accounts, and tokens
- Implement behavioral monitoring: Detect unusual patterns indicating AI activity
- Train your workforce: Educate on AI-enhanced social engineering tactics
Strategic investments:
- AI-driven threat detection platforms (like Trend Vision One, CrowdStrike Falcon)
- Continuous risk exposure management systems
- Zero-trust architecture covering both human and machine identities
- Incident response automation to match attacker speed
- Threat intelligence focused on agentic attack patterns
For Law Enforcement & Regulators
- Develop frameworks for investigating autonomous criminal systems, not just individuals
- International cooperation to combat distributed, self-healing criminal infrastructure
- Update laws to address AI agent criminal liability
- Resource allocation for AI-powered forensic capabilities
- Public awareness campaigns about agentic threat landscape
Conclusion: The Dawn of Autonomous Cybercrime
We stand at an inflection point. The transformation from "Cybercrime-as-a-Service" to "Cybercrime-as-a-Sidekick" represents more than a technological evolution—it's a fundamental restructuring of how criminal enterprises operate.
The Nexus Event Approaches
All indicators suggest we're nearing the "Nexus Event"—the rapid, ecosystem-wide adoption of agentic AI by criminals:
✅ Technology matured: Tools are accessible via no-code platforms
✅ Profitability proven: Early adopters demonstrate superior returns
✅ Criminal pressure: Traditional methods face declining success
✅ Barrier reduction: Technical skills no longer required
When this nexus arrives, the attack landscape will transform overnight—not gradually.
The Choice Before Us
The security community, businesses, and individuals face a clear decision:
Option 1: Wait and react after agentic criminal operations become standard
Result: Years of playing catch-up, massive financial losses, undermined trust
Option 2: Invest now in AI-powered defenses and resilience
Result: Prepared infrastructure, trained workforce, competitive advantage
A Call to Action
The Trend Micro researchers emphasize: "Organizations will encounter entirely new categories of cyberattacks that were previously technically or economically infeasible prior to the advent of artificial intelligence capabilities."
These aren't theoretical future threats. They're happening now:
- Anthropic disrupted AI-orchestrated espionage in September 2025
- Dragonforce offers AI-powered ransom analysis services today
- CrowdStrike tracks 265+ attack groups, many experimenting with agentic AI
- Verizon reports AI-assisted attacks doubled in two years
Final Thoughts
The good news: Defensive AI is advancing rapidly, and organizations investing now can build robust protection.
The concerning news: The window is closing. Once criminal agentic systems achieve widespread adoption, the volume and sophistication of attacks will overwhelm unprepared defenses.
The question isn't whether agentic AI will transform cybercrime—it's whether we'll be ready when it does.
Stay vigilant. Stay informed. Stay protected.
Additional Resources
For Further Reading
- Trend Micro Full Report: "VibeCrime: Preparing Your Organization for the Next Generation of Agentic AI Cybercrime"
- Anthropic Threat Report: "Detecting and Countering Misuse of AI: August 2025"
- Malwarebytes: 2025 State of Malware Report
- CrowdStrike: 2025 Threat Hunting Report
- World Economic Forum: "Non-Human Identities: Agentic AI's New Frontier of Cybersecurity Risk"
About ScamWatchHQ: We track emerging fraud tactics and provide actionable intelligence to help individuals and organizations protect themselves from evolving threats. Our research team monitors global scam trends, cybercriminal innovation, and defensive strategies to keep our community informed and secure.
Article last updated: December 11, 2025





