The Identity Theft Crisis Demands Personal Action
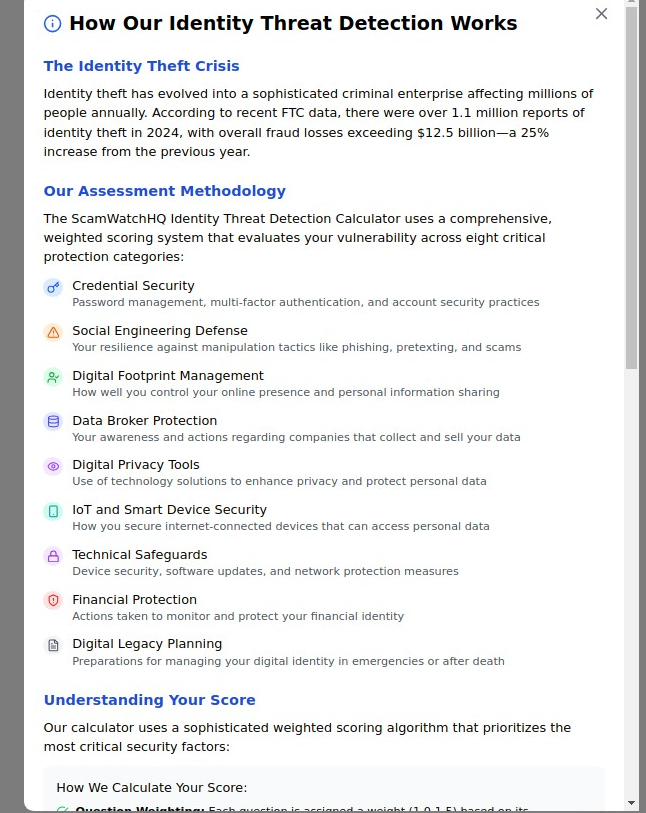
Identity theft has evolved into a sophisticated criminal enterprise affecting millions of people annually. According to recent FTC data, there were over 1.1 million reports of identity theft in 2024, with overall fraud losses exceeding $12.5 billion—a 25% increase from the previous year. What makes this crisis particularly dangerous is that most victims don’t realize they’re vulnerable until after criminals have already struck.
Identity Threat Detection Calculator | Assess Your RiskTake our free assessment to discover your personal identity security risk score and get personalized recommendations.Identity Threat Detection Calculator
 Unlike other crimes that require physical proximity or opportunity, identity theft operates in the digital shadows. Criminals can exploit your personal information from anywhere in the world, often using data you unknowingly shared or that was collected without your explicit consent. The average victim spends over 200 hours and $1,400 recovering from identity theft—time and money that could be saved through proactive protection.
Unlike other crimes that require physical proximity or opportunity, identity theft operates in the digital shadows. Criminals can exploit your personal information from anywhere in the world, often using data you unknowingly shared or that was collected without your explicit consent. The average victim spends over 200 hours and $1,400 recovering from identity theft—time and money that could be saved through proactive protection.
Why Standard Security Advice Falls Short
Most identity protection guidance focuses on obvious steps like “use strong passwords” and “monitor your credit report.” While these basics are important, they address only a fraction of your actual identity risk profile. Modern identity theft operates across multiple attack vectors that require comprehensive protection strategies.
The reality is that criminals don’t just target one vulnerability—they exploit whatever weakness they can find in your digital life.
The Nine Critical Identity Security Categories
Effective identity protection requires addressing vulnerabilities across your entire digital ecosystem:
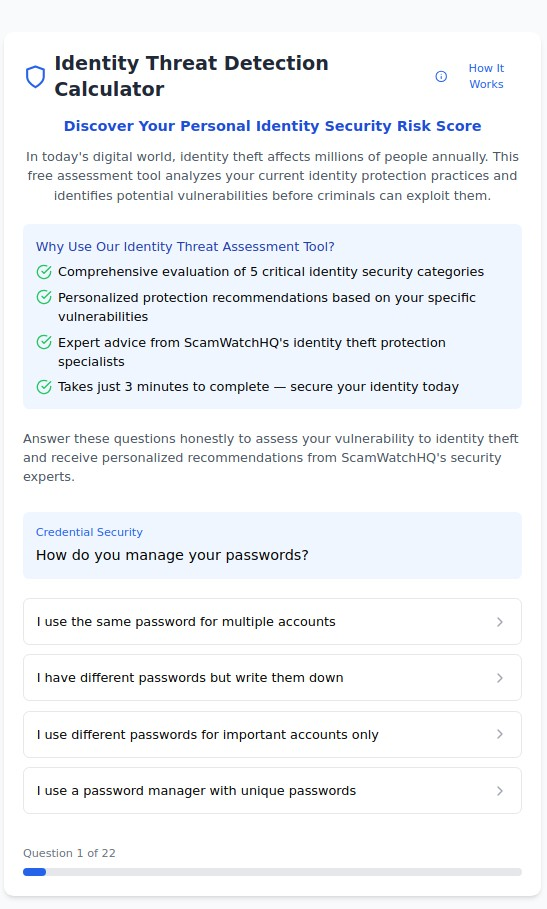
1. Credential Security Your first line of defense against account takeovers and unauthorized access. This includes password management practices, multi-factor authentication usage, and account security configurations across all your online services.
2. Social Engineering Defense Your ability to recognize and resist manipulation tactics used by scammers, including phishing emails, pretexting phone calls, romance scams, and sophisticated impersonation attempts.
3. Digital Footprint Management How well you control the personal information available about you online, from social media profiles to public records and data aggregation sites.
4. Data Broker Protection Your awareness of and actions regarding the hundreds of companies that legally collect, compile, and sell detailed profiles of your personal information.
5. Digital Privacy Tools Your use of technology solutions like VPNs, encrypted messaging, privacy-focused browsers, and other tools that enhance your personal data protection.
6. IoT and Smart Device Security How you secure Internet-connected devices in your home and life that can access or reveal personal information, from smart speakers to connected cars.
7. Technical Safeguards Your device security practices, including software updates, antivirus protection, secure network usage, and backup strategies.
8. Financial Protection Specific actions you’ve taken to monitor and protect your financial identity, including credit monitoring, fraud alerts, and account security measures.
9. Digital Legacy Planning Your preparations for managing your digital identity during emergencies, incapacitation, or after death—an often-overlooked area that can create significant vulnerabilities for both you and your family.
Identity Threat Detection Calculator | Assess Your RiskTake our free assessment to discover your personal identity security risk score and get personalized recommendations.Identity Threat Detection Calculator

The Sophisticated Nature of Modern Identity Threats
Beyond Simple Data Breaches
While data breaches make headlines, the most dangerous identity threats often come from more subtle sources:
Social Media Intelligence Gathering: Criminals systematically harvest information from your social media profiles, building detailed pictures of your life, relationships, and vulnerabilities that enable highly targeted attacks.
Data Broker Aggregation: Legal data broker companies collect information from hundreds of sources, creating comprehensive profiles that criminals can purchase or hack to access.
IoT Device Exploitation: Smart home devices, fitness trackers, and connected cars collect intimate details about your daily routines, location patterns, and personal habits.
Business Email Compromise: Criminals target your workplace email and systems to gather personal information and launch attacks against both you and your employer.
Advanced Attack Techniques
Modern identity criminals use sophisticated techniques that bypass traditional security measures:
Synthetic Identity Creation: Combining real and fake information to create new identities that can bypass fraud detection systems for months or years.
Account Takeover Chains: Using access to one compromised account to systematically gain control of your entire digital life through password resets and authentication bypasses.
Relationship Exploitation: Targeting family members, friends, or colleagues to gather information about you or gain access to your accounts through social engineering.
Long-Term Reconnaissance: Spending weeks or months gathering information about high-value targets before launching coordinated attacks.
Identity Threat Detection Calculator | Assess Your RiskTake our free assessment to discover your personal identity security risk score and get personalized recommendations.Identity Threat Detection Calculator

Why You Need a Comprehensive Risk Assessment
Personal Vulnerability Varies Dramatically
Your identity risk profile depends on numerous factors that generic security advice can’t address:
- Your professional role and public visibility- The amount of personal information you’ve shared online over the years- Your family situation and dependents- Your financial assets and transaction patterns- The types of devices and services you use daily- Your geographic location and travel patterns
One Size Fits All Doesn’t Work
A corporate executive with significant online presence faces different threats than a retiree with minimal digital footprint. A parent with teenage children has different vulnerabilities than a single professional. Effective identity protection requires understanding your specific risk factors and tailoring protections accordingly.
Early Detection Prevents Damage
Most identity theft victims discover the crime only after significant damage has occurred—fraudulent accounts opened, credit scores damaged, or finances compromised. Proactive risk assessment identifies vulnerabilities before criminals can exploit them, allowing you to address weaknesses on your timeline rather than responding to a crisis.
How Our Identity Threat Detection Calculator Works
Comprehensive Multi-Category Analysis
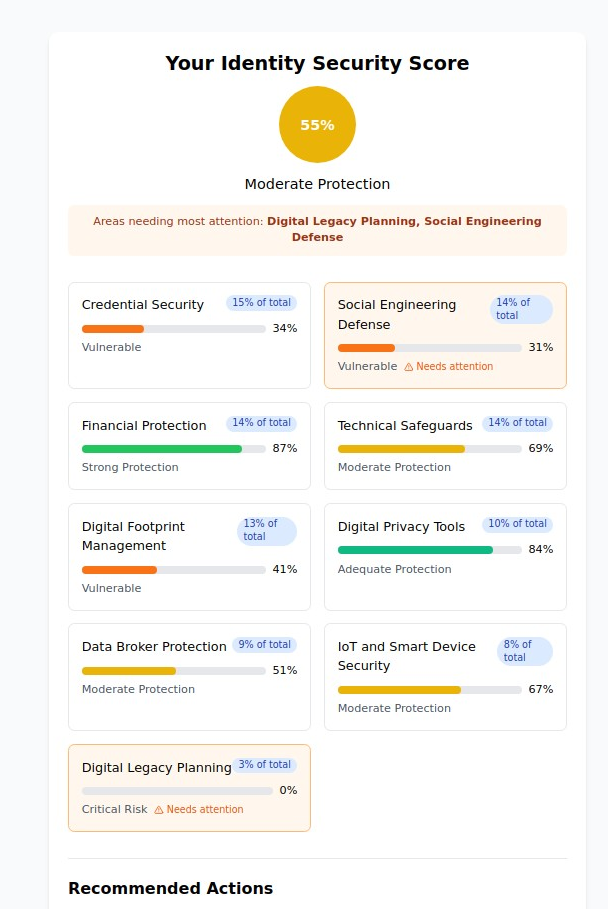
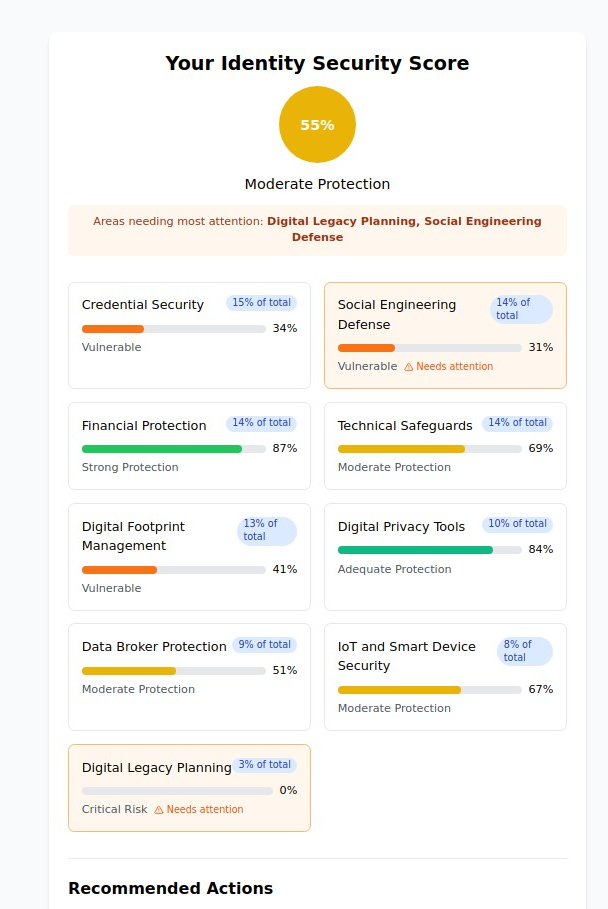
Our assessment uses a sophisticated, weighted scoring system that evaluates your vulnerability across all nine critical protection categories. Unlike simple checklists, the calculator considers how different vulnerabilities interact and compound to create overall risk.
Personalized Risk Scoring
The assessment provides specific percentage scores for each category, showing exactly where you’re well-protected and where you need immediate attention. You’ll see both individual category scores and an overall identity security rating.
Actionable Priority Recommendations
Rather than overwhelming you with generic security advice, the assessment identifies your highest-risk areas and provides specific, prioritized recommendations based on your actual vulnerabilities. Focus your efforts where they’ll have the greatest impact on your personal security.
Expert-Backed Methodology
The assessment methodology is developed by identity theft protection specialists who understand both the criminal techniques used in modern identity theft and the practical realities of personal security implementation.
What Your Assessment Results Reveal
Immediate Risk Areas
The assessment identifies categories where you’re currently vulnerable to identity theft, helping you understand which aspects of your digital life need immediate attention.
Protection Strengths
Recognize areas where you’re already well-protected, so you can maintain those practices and focus improvement efforts on genuine weaknesses.
Weighted Risk Analysis
Understand not just what’s vulnerable, but what’s most important to protect based on the potential impact of compromise in different categories.
Implementation Priorities
Receive specific guidance on which security improvements to tackle first for maximum protection benefit with minimum effort and cost.
Taking Action: From Assessment to Protection
Quick Wins for Immediate Improvement
Most assessments reveal several security improvements that can be implemented immediately:
- Enabling multi-factor authentication on critical accounts- Updating privacy settings on social media platforms- Installing essential privacy tools and browser extensions- Setting up basic financial monitoring and fraud alerts- Securing smart devices with strong passwords and updated firmware
Strategic Long-Term Planning
Comprehensive identity protection often requires longer-term planning:
- Systematic removal of personal information from data broker sites- Implementation of advanced privacy tools and techniques- Development of digital legacy and emergency access plans- Regular monitoring and assessment to address new threats- Family-wide security awareness and protection strategies
Professional Service Considerations
While self-assessment and DIY implementation work for many people, some situations benefit from professional identity protection services:
- High-visibility individuals facing targeted threats- Business owners whose personal and professional identities are interlinked- Families dealing with ongoing stalking or harassment- People who’ve already experienced identity theft and need comprehensive recovery- Individuals who lack time or technical skills for comprehensive self-protection
The Privacy Protection Connection
Understanding Data Collection and Use
Modern identity threats often stem from the massive collection and use of personal data by legitimate companies. Understanding how your information is collected, stored, and shared helps you make informed decisions about privacy protection.
Taking Control of Your Digital Footprint
Effective identity protection requires active management of your online presence. This includes not just what you share, but understanding what others share about you and how aggregated data creates detailed profiles of your life.
Privacy as Security
Privacy tools and practices aren’t just about keeping information secret—they’re active security measures that reduce your exposure to identity theft by limiting the information available to criminals.
Identity Threat Detection Calculator | Assess Your RiskTake our free assessment to discover your personal identity security risk score and get personalized recommendations.Identity Threat Detection Calculator

The Cost of Inaction
Financial Impact Beyond Direct Theft
Identity theft costs extend far beyond money stolen from accounts:
- Time spent recovering and restoring your identity- Legal fees for resolving fraudulent accounts and charges- Increased insurance premiums and loan interest rates- Lost opportunities due to damaged credit or reputation- Ongoing monitoring and protection service costs
Emotional and Relationship Toll
Identity theft victims often experience:
- Stress and anxiety about ongoing vulnerability- Relationship strain when family members are also affected- Loss of trust in digital services and online interactions- Feeling of violation and loss of privacy- Ongoing concern about future attacks
Professional and Reputation Consequences
For many people, identity theft affects more than personal finances:
- Professional reputation damage if business accounts are compromised- Security clearance implications for government and contractor employees- Client or customer trust issues for business owners- Social media and online reputation attacks- Long-term digital footprint contamination
Your 3-Minute Identity Security Assessment
Understanding your personal identity risk doesn’t require hours of research or expensive professional consultations. Our Identity Threat Detection Calculator provides comprehensive analysis in just 3 minutes, with immediate results and actionable recommendations.
The assessment covers: ✓ All nine critical identity security categories ✓ Personalized risk scoring based on your specific vulnerabilities ✓ Priority recommendations for maximum security improvement ✓ Expert guidance from identity theft protection specialists ✓ Immediate results with no waiting or account creation required
Your identity security assessment is completely private—all processing happens locally in your browser with no data stored or transmitted.
Ready to discover your identity security risk score?
Frequently Asked Questions
How accurate is the risk assessment? The assessment uses proven methodologies developed by identity theft protection specialists and is based on analysis of millions of identity theft cases. While no assessment can predict specific attacks, it accurately identifies the types of vulnerabilities that criminals most commonly exploit.
Will this assessment help if I’ve already been a victim of identity theft? Yes, the assessment is valuable both for prevention and recovery. It helps identify ongoing vulnerabilities that may have contributed to past incidents and ensures you’re protected against future attacks.
How often should I reassess my identity security? We recommend reassessment whenever you make significant changes to your digital life—new social media accounts, major purchases, job changes, or family status changes. Many people find annual assessments helpful for maintaining ongoing security awareness.
Is the assessment really free? Yes, the complete assessment and personalized recommendations are provided at no cost. This is part of our commitment to helping people protect themselves against identity theft. There are no hidden fees, upsells, or required purchases.
What if I score poorly on the assessment? Don’t panic—most people have significant room for improvement in identity security. The assessment provides specific, prioritized recommendations that you can implement gradually. Even small improvements significantly reduce your risk of becoming an identity theft victim.
*Take control of your identity security today. In just 3 minutes, you’ll know exactly where you stand and what steps to take to protect yourself from the growing threat of identity theft.
Identity Threat Detection Calculator | Assess Your RiskTake our free assessment to discover your personal identity security risk score and get personalized recommendations.Identity Threat Detection Calculator